Understanding ransomware attacks and data breaches in fintech
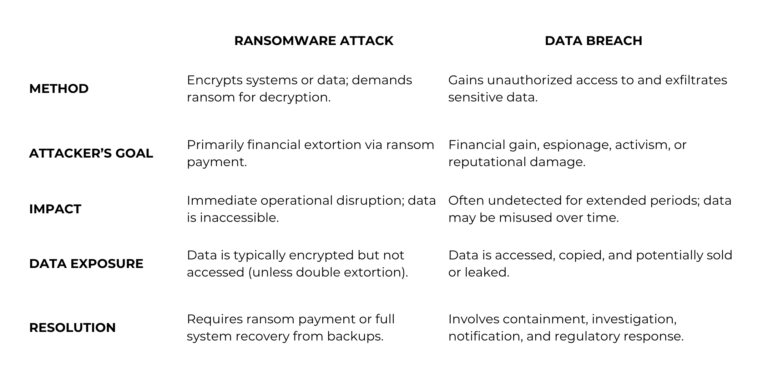
Ransomware attacks and data breaches are among the most critical cybersecurity challenges fintech companies face today. Although often grouped together, these threats differ in how they operate, the kind of damage they cause, and how organizations need to respond.
In both cases, financial gain is a key motive, but the landscape is evolving. Attackers are blending techniques, pursuing ideological or political agendas, and leveraging ever more sophisticated methods to breach fintech systems.
As attackers become more sophisticated, fintech companies must move beyond traditional defense models and adopt a proactive, tailored cybersecurity strategy, a strategy that aligns with the unique operational realities of financial platforms.

Ransomware attacks and data breaches: Key differences
Understanding ransomware attacks
These attacks begin when malicious actors deploy malware to encrypt critical files or systems, rendering them unusable. The attackers then demand a ransom in exchange for a decryption key. Increasingly, these attacks involve data exfiltration before encryption, allowing attackers to threaten public leaks if the ransom is not paid. This tactic is known as double extortion.
In 2024, the financial services sector saw the highest-ever rate of ransomware incidents, according to industry reports. The most common attack vectors included:
- Compromised user credentials
- Unpatched vulnerabilities
- Phishing and malicious email links
- Misconfigured access points
- Brute-force entry methods
Understanding data breaches
Data breaches, by contrast, involve unauthorized access to sensitive information, often without causing immediate disruption. The stolen data can include:
- Personal identifiable information (PII)
- Financial records
- Authentication tokens
- Proprietary business assets.
While many breaches are financially motivated, they are increasingly linked to espionage, ideological activism, and reputational sabotage.
These breaches are not only growing in frequency, they’re also expensive. The average cost of a data breach in the financial sector has reached $6.08 million, with long-tail consequences that include regulatory fines, customer attrition, and erosion of trust.
What drives these attacks?
While many assume that all cyberattacks are financially motivated, the reality is more complex. In the fintech sector, sensitive data and high-trust platforms make organizations attractive for a wide range of reasons.
Ransomware attacks: Extortion with a twist
The primary goal of most ransomware attacks remains financial extortion. Attackers encrypt mission-critical systems and demand payment, in exchange for restoring access. But in recent years, their tactics have evolved:
- Double extortion: Before encrypting data, attackers exfiltrate it and threaten to publish or sell it unless the ransom is paid.
- Operational disruption: Some ransomware campaigns focus on causing chaos, halting financial services or critical infrastructure, often for political or ideological reasons.
- Espionage and data theft: While less common, certain advanced ransomware groups are using encryption as a smokescreen for deeper, stealthier data theft operations.
Data breaches: Quiet, targeted, and often ideological
Though less immediately visible than ransomware, data breaches can cause equally severe long-term damage. Motivations behind breaches include:
- Financial gain: Stealing sensitive personal or financial data to commit fraud, identity theft, or resell on darknet marketplaces.
- Corporate espionage: Targeting trade secrets, proprietary algorithms, or business strategies for competitive advantage.
- Hacktivism: Breaches driven by political or social causes, aimed at exposing or disrupting organizations viewed as unethical or controversial.
- Reputation damage or sabotage: Designed to erode public trust or destabilize operations.
- Insider threats: Disgruntled employees or contractors with legitimate access who leak or sell data for personal or ideological reasons.
Recent incidents in the fintech ecosystem
Several high-profile attacks in the last two years highlight how fintech companies, regardless of size or geography, are vulnerable:
- Harvest (France, 2025): A renowned French fintech company was targeted by ransomware group Run Some Wares, leading to data theft involving internal documents and client records.
- C-Edge Technologies (India, 2024): A ransomware attack disrupted core banking services for over 300 small banks, triggered by a misconfigured third-party server.
- Finastra (UK, 2024): One of the world’s largest fintechs suffered a breach via a secure file-transfer platform, impacting over 400 clients.
- Truist Bank (U.S., 2024): A data breach exposed employee records, which were later listed for sale on the dark web.
- Globalcaja (Spain, 2023): The Play ransomware group encrypted critical systems and stole sensitive personal and business documents, leading to temporary branch closures.
These incidents reveal an uncomfortable truth: even institutions with mature cybersecurity programs are not immune. The sophistication and adaptability of threat actors are outpacing traditional defenses.
Evaluating the effectiveness of current cybersecurity measures
Most financial institutions have invested heavily in cybersecurity. Multi-factor authentication (MFA), secure access controls, endpoint detection and response (EDR), and regular risk assessments are now considered standard. Some firms are also deploying AI-driven anomaly detection systems to identify threats in real time.
But most security measures are compliance-oriented, not attack-oriented, which is why attackers continue to find ways in. Attackers are increasingly using zero-day vulnerabilities, multi-vector entry points, and supply chain compromises to bypass defenses.
It’s clear that while cybersecurity capabilities have matured, the threat landscape has evolved faster, demanding a more tailored and anticipatory approach. More fintech companies are looking beyond prevention and detection, and towards exposure-based defense strategies.
Instead of waiting for an alert, they’re asking: “Where could an attacker get in, and how far could they go if they did?”
Building resilience with a fintech-first security strategy
Defending a fintech platform is not the same as defending a traditional enterprise. Between open APIs, embedded finance, rapid product iteration, cryptocurrencies, and high-value data flows, the security demands are unique and constantly evolving.
At Clovr Labs, we approach cybersecurity from inside the fintech ecosystem. We’ve built platforms, scaled products, and dealt with compliance realities ourselves, which means our solutions are rooted in how fintechs actually operate.
Our methodology focuses on:
- Mapping real exposure across your stack.
- Simulating how attackers would exploit it.
- Designing defenses that adapt to your business model, not disrupt it.
This is what we call non-linear, liquid security: agile protection built for fast-moving fintechs.
If you’re still relying on generic cybersecurity frameworks, it’s time to rethink your strategy. Attackers already have.
Don’t wait for an attack to test your defenses. Let’s map your risk now before someone else does.







