How to prevent phishing and smishing scams in fintech
Phishing and smishing scams are an industrialized attack vector targeting businesses and their clients with increasing precision. In just the last six months, phishing-related emails have surged by 341%, and financial losses linked to these attacks topped $17.4 billion globally in 2024, a staggering 45% increase from the previous year.
For fintech companies, these attacks pose a dual threat: they compromise internal operations and erode client trust. Phishing and smishing are among today’s most critical cybersecurity challenges, so it’s of vital importance to know what your company can do to stay ahead of them.

What is Phishing?
Phishing is a form of cyberattack where criminals impersonate legitimate institutions to trick victims via email into revealing sensitive data such as login credentials, financial information, or security codes. These emails often look like urgent messages from trusted entities: a bank alert, a payment request, or a system security notification.
In the fintech sector, phishing attacks are especially dangerous. A single spoofed message that mimics your brand could trick users into handing over credentials or making unauthorized transactions, damaging both your security and your reputation.
Most common phishing scams in the fintech sector
Phishing tactics have evolved well beyond clumsy misspelled emails. Today’s attackers use tailored messaging, corporate-style branding, and even AI to mimic fintech companies with frightening accuracy.
Here are some of the most common phishing scams targeting fintech businesses and their clients:
Credential harvesting
Fake login pages that mirror fintech portals (banking apps, crypto wallets, payment platforms) are sent via email to trick users into entering their usernames and passwords.
Business Email Compromise (BEC)
Cybercriminals spoof or hijack the email accounts of executives or vendors to send convincing payment requests or internal access instructions, often leading to fraudulent transfers or data breaches.
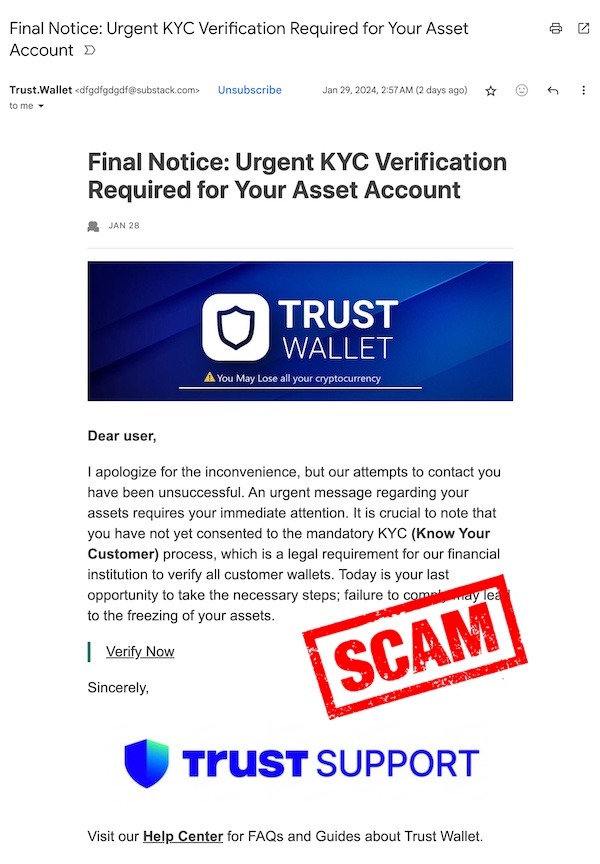
Fake KYC/AML requests
Attackers send fraudulent messages requesting Know Your Customer (KYC) or Anti-Money Laundering (AML) information, targeting both internal teams and clients with a sense of legal urgency.
Compliance or security alerts
Emails that mimic internal IT or external regulatory bodies, prompting recipients to “update credentials” or “confirm security settings” under the threat of account suspension.
Invoice or payment fraud
Scammers send what appear to be overdue invoices or payment requests from vendors or partners, often with realistic-looking PDFs or links that lead to malware or data capture sites.
What is smishing?
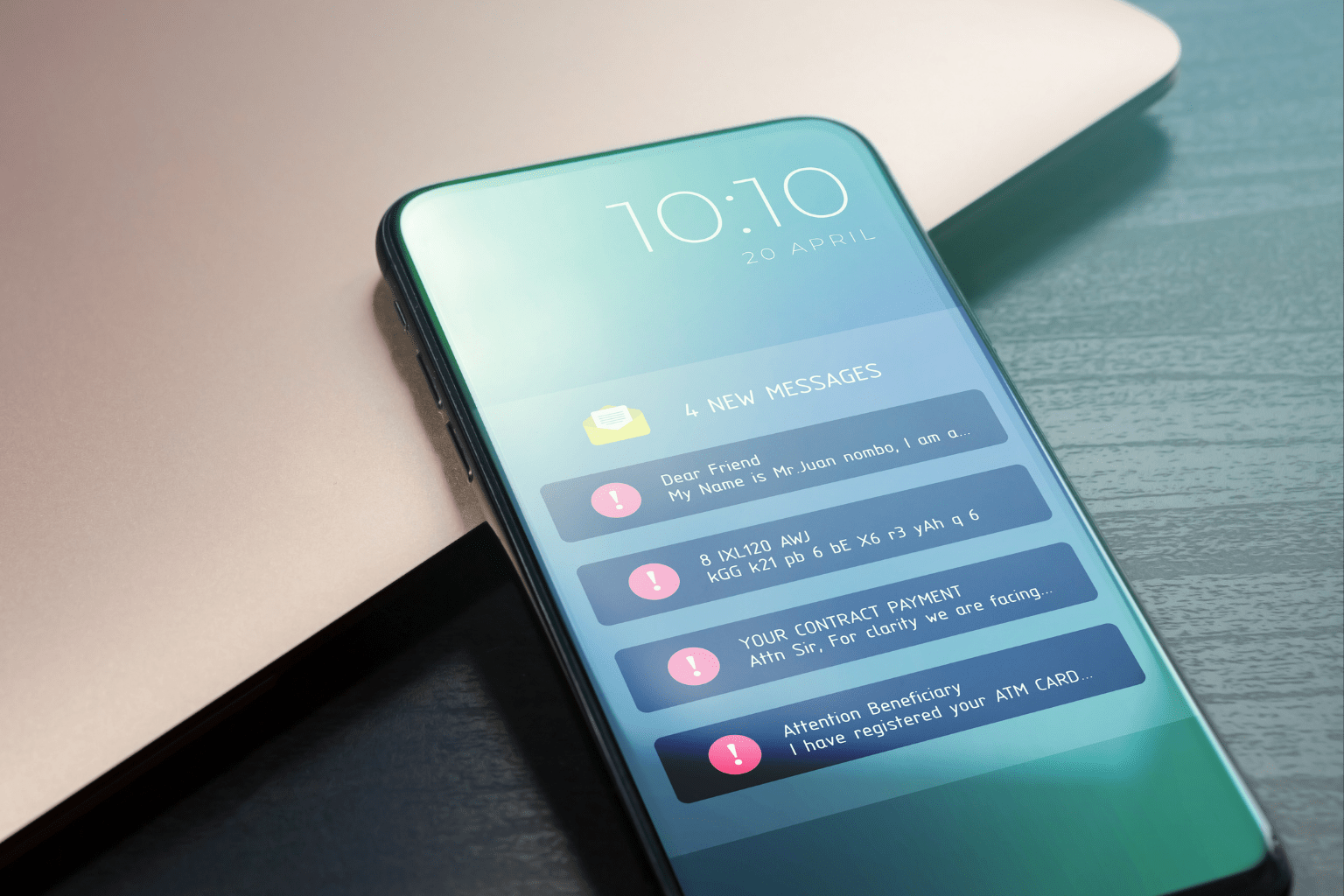
Smishing, or “SMS phishing,” is a form of cyberattack that uses deceptive text messages to trick recipients into revealing sensitive information, clicking malicious links, or downloading malware. These attacks often impersonate trusted institutions like banks, digital wallets, or fintech platforms, and rely on urgency, fear, or financial incentives to drive action.
What makes smishing especially dangerous today is how sophisticated it has become. Attackers are no longer sending messages from random or unknown numbers. Increasingly, they’re exploiting weaknesses in SMS infrastructure to impersonate a company’s actual sender ID, making it appear as though the message truly comes from your brand. In many cases, these fake messages even appear within the same SMS thread as previous legitimate communications, making them nearly indistinguishable from the real thing.
For fintech companies, this evolution is a serious threat. It not only puts clients at risk of fraud, but also damages the trust and credibility of your communication channels, especially if customers can no longer tell which messages are real.
Most common smishing scams in the fintech sector
Smishing attacks are crafted with highly targeted messages that look legitimate, often replicating the tone, branding, and urgency of real communications from fintech providers.
Here are the most common types of smishing scams threatening your clients and your company:
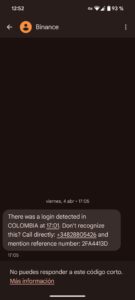
Fake fraud alerts
Attackers pose as your fraud prevention team, warning the recipient of “suspicious activity” and urging them to click a link or call a number to verify their account. These scams often use real customer data leaked from previous breaches to increase credibility.
Two-factor authentication interception
A user receives a message appearing to be from your platform, asking them to confirm or resend a one-time password (OTP) for account access. In reality, attackers are trying to intercept codes during a live phishing session.
Loan or payment scams
Messages promising quick loan approval or confirming a large outgoing payment. The links lead to fake login portals or malware downloads, targeting both retail clients and business users.
KYC verification requests
Customers receive urgent SMS alerts claiming their account access is suspended due to missing KYC documents. They’re asked to upload ID or banking details through a spoofed page.
Fake app update or account lockout notices
These messages trick users into downloading fake “app updates” outside of official app stores or claim their account will be locked if they don’t act immediately, leading to credential theft or malware infection.
How do phishing and smishing scams happen?
Both phishing and smishing rely on social engineering, manipulating human behavior rather than breaking through technical defenses. Attackers exploit trust, urgency, and fear to push users into quick, unthinking actions.
Here’s a breakdown of how these scams typically unfold:
- Reconnaissance: Attackers gather information about your company, employees, and clients via social media, leaked data, or public platforms.
- Impersonation: Using spoofed email addresses or SMS sender IDs, they mimic your brand or internal teams.
- Deception: Messages are crafted to appear urgent or threatening (e.g., account lockouts, fraud alerts), prompting users to act fast.
- Engagement: Victims are lured to click malicious links, enter credentials, or share sensitive information.
- Exfiltration or fraud: Once data is captured, attackers use it for unauthorized access, financial theft, or further targeted attacks.
Top practices to prevent phishing and smishing scams
Preventing phishing and smishing requires building layered defenses that address both internal risks and client vulnerabilities. Here’s how you can protect your company and your customers:
Internal measures (protecting your company)
- Offer regular training to help teams recognize phishing and smishing attempts, especially for high-risk roles like C-level, finance, support, and IT.
- Execute phishing and smishing simulations to test your team’s response readiness, identify gaps, and reinforce best practices.
- Deploy email and SMS filtering tools and threat detection systems that flag suspicious content before it reaches inboxes or devices.
- Implement and enforce authentication protocols to protect your domain from spoofing and impersonation.
- Have a clear, practiced incident response protocol for isolating, reporting, and containing attacks when they happen.
External measures (protecting your customers)
- Use verified and registered sender IDs to protect and reduce the risk of impersonation.
- Encourage secure in-app messaging so communication comes via your official app or platform, where you control the environment and authentication.
- Proactively educate customers on how to recognize scams, especially during onboarding and through ongoing alerts.
- Have a consistent messaging style in customer comms so that anything that looks off is easier to spot.
- Avoid relying on SMS for login, verification, or transactional alerts when possible. Instead, use more secure, app-based authentication methods.
What to do if your company becomes a victim of phishing or smishing
Even with strong defenses, no company is immune. If an attack slips through, quick, calm, and clear action can stop an incident from becoming a crisis.
1. Contain the incident: Isolate affected systems or accounts immediately to prevent further damage.
2. Alert internal teams: Notify IT, security, and customer support. A coordinated response is key.
3. Communicate with clients: Be transparent, but controlled. Inform affected users and offer guidance on next steps, preferably via your official app or secure channels.
4. Investigate and report: Analyze the breach to understand what happened and report it to the relevant authorities.
5. Review and reinforce: Patch vulnerabilities, update protocols, and run a post-mortem to improve future resilience.
How Clovr Labs helps fintech companies prevent phishing and smishing
At Clovr Labs, we focus on prevention through proactive, multi-layered security, helping fintech companies stay ahead of phishing and smishing scams with solutions designed to identify and eliminate vulnerabilities before they’re exploited. Here’s how:
- Threat Mapping: We identify where your company and clients are most exposed to phishing and smishing risks, from spoofable domains to vulnerable communication flows.
- 360º Exposure Analysis: Our audits reveal weak points across your entire digital ecosystem, allowing you to close security gaps before attackers find them.
- Non-Linear Defense: We build adaptive, real-world defenses based on how your business communicates, internally and with customers.
Contact Clovr Labs to assess your company’s exposure and build a prevention-first strategy.